The project THE CASCADE will be organized in five tasks as despicted in the following picture.
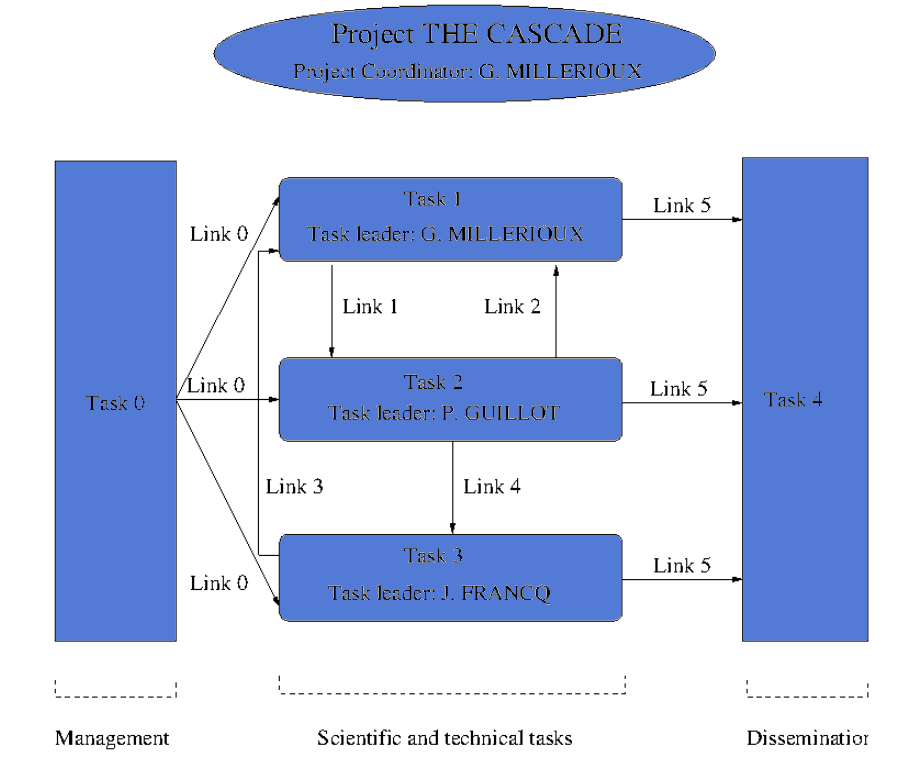
- Task 1: Synchronization
Task leader: Gilles Millérioux.
Task 1 is mostly devoted to the investigation of the master-slave setup which must get the self-synchronization property. It has been stress that self-synchronization can be viewed, from a control theory point of view, as an unknown input state reconstruction problem and/or a left inversion problem.
Also flatness appears as an original and new solution for the design of SSS.This issue must be particularized to specific dynamical systems, that is specific nonlinearities which are suitable regarding the cryptographic context. More specifically, the security and the implementation feasibility should be taken into account.
- Task 2: Theoretical Security Assessment
Task leader: Philippe Guillot.
Task 2 is mostly devoted to the investigation of the master-slave setup that must agree with cryptographic issues, in particular the security criteria from a theoretical point of view. Hence, the goal of this task is to ensure that the algorithms are strong enough against cryptanalysis attacks. The architectures derived from Task 1 will be extensively studied in Task 2. First, the statistical qualities of the ciphers will be tested as a preliminary step of this task, and then shifted through all known or specifically tailored cryptanalytic techniques.
- Task 3: Hardware-oriented issues [Implementation results]
Task leader: Julien Francq.
This task is also devoted to the investigation of points the master-slave setup which must agree with cryptographic issues. In this Task 3, security will be investigated in terms of strength and weakness against physical attacks. The objective of applicability in a real-world context will be considered as well.
The main goals of Task 3 are:
- to provide Task 1 with specifications of the ciphers regarding the targeted applications
- to investifate the complexity, properties and performances of the SSSC and its convenience for operational usage
- to look into scientific issues related to hardware implementation specificities, in particular the assessment of the strength against physical attacks, more specifically Side Channel Attacks (SCA).